In the vast landscape of the internet, search engines like Google serve as gateways to an immense repository of information. While most users employ search queries to find specific content, a subset of advanced search techniques is known as “Google Dorks.”
These specialized search strings enable users to perform targeted searches and uncover hidden information that may not be accessible through conventional search queries.
Google Dorks, also called Google hacking or Google Dorking, leverage advanced search operators and syntax to refine search results and uncover sensitive data or website vulnerabilities.
Initially used by security researchers and penetration testers to identify potential security risks, Google Dorks have gained popularity among cybercriminals and hackers for reconnaissance purposes.
In this Techblogwiki article, we delve into Google Dorks, exploring what they are, how they work, and their implications for online security and privacy. By understanding the fundamentals of Google Dorks, users can better navigate the complexities of internet search and safeguard their digital assets from potential threats.
Join us as we unravel the intricacies of Google Dorks and shed light on their role in the ever-evolving cybersecurity landscape.
What Are Google Dorks?

Google Dorks, also known as Google hacking or Google Dorking, are specialized search queries that leverage advanced search operators and syntax to retrieve specific information from search engine databases.
These queries allow users to narrow down search results and uncover hidden or sensitive information that may not be accessible through conventional search queries.
Initially utilized by security professionals, researchers, and penetration testers to identify potential vulnerabilities and security risks on websites, cybercriminals, and hackers have also adopted Google Dorks for reconnaissance purposes.
By crafting precise search queries, users can discover exposed data, misconfigured servers, login credentials, and other potentially sensitive information.
Google Dorks can be used to search for various types of information, including:
- Vulnerable web servers and services
- Exposed databases and directories
- Login pages with default credentials
- Confidential documents and files
- Network devices with known vulnerabilities
While Google Dorks can be a powerful information-gathering and analysis tool, they pose security risks when used maliciously. Therefore, organizations and individuals need to be aware of the potential implications of Google Dorks and take proactive measures to secure their online assets.
How Does Google Dorking Work?
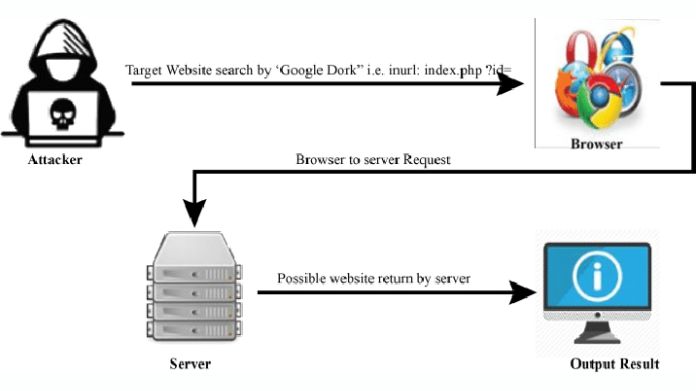
Google Dorking uses advanced search operators and syntax to refine search queries and retrieve specific information from search engine databases.
Here’s how it works:
1. Advanced Search Operators: Google Dorking uses advanced search operators, special characters, or commands that modify the search query to produce more targeted results. These operators allow users to specify file types, website domains, and keywords.
2. Syntax and Query Crafting: Users craft custom search queries using keywords, operators, and syntax. By structuring the query in a specific way, users can narrow down search results and uncover hidden or sensitive information that may not be readily accessible through conventional search queries.
3. Targeted Searches: Google Dorks are designed to target specific website information or vulnerabilities. For example, users can search for exposed directories, vulnerable web servers, login pages with default credentials, or confidential documents.
4. Analysis and Exploration: Once the search query is executed, users analyze the search results to identify potential security risks, vulnerabilities, or exposed data. This process often involves exploring multiple search results pages and refining the query to retrieve more relevant information.
5. Security Implications: While Google Dorking can be used for legitimate purposes such as security research and penetration testing, it maliciously poses security risks. Cybercriminals and hackers may exploit Google Dorks to discover sensitive information or exploit website vulnerabilities.
Overall, Google Dorking is a powerful information-gathering and analysis technique, but it requires careful consideration of ethical and security implications when used. Organizations and individuals should know the potential risks associated with Google Dorking and take appropriate measures to secure their online assets.
Examples of Google Dork
Google Dorks are specialized search queries that leverage advanced search operators and syntax to retrieve specific information from search engine databases.
Here are some examples of Google Dorks:
Site-specific Search: site:example.com intitle:”index of” filetype:pdf
Filetype Search: filetype:pdf “confidential”
Vulnerable Web Servers: intitle:”Apache Tomcat” “HTTP Status 500” -site:tomcat.apache.org
Exposed Directories: intitle:”Index of /” “parent directory”
Login Pages with Default Credentials: intitle:”login” “username” “password”
Confidential Documents: intitle:”confidential” filetype:doc
Network Devices with Known Vulnerabilities: intitle:”index of” “Nessus Scan Report” filetype:txt
CCTV Cameras: inurl:/view/index.shtml
Exposed Database Files: intitle:”Index of” “database.sql”
Login Pages with SQL Injection Vulnerabilities: inurl:login.php?id= intext:”SQL injection”
These examples demonstrate how Google Dorks can be used to search for various types of information, including exposed directories, vulnerable web servers, login pages with default credentials, confidential documents, and more.
It’s important to note that while Google Dorks can be used for legitimate purposes such as security research, they also pose security risks when used maliciously. Therefore, users should exercise caution and adhere to ethical guidelines when using Google Dorks for information gathering.
Wrapping Up!!
Google Dorks are specialized search queries that use advanced operators to find specific information in search engine databases. They are valuable for security research but also pose risks if used maliciously.
Understanding their function involves crafting precise queries to uncover hidden data or vulnerabilities on websites. Users must be cautious and ethical when using Google Dorks to avoid potential security breaches.






